How it works
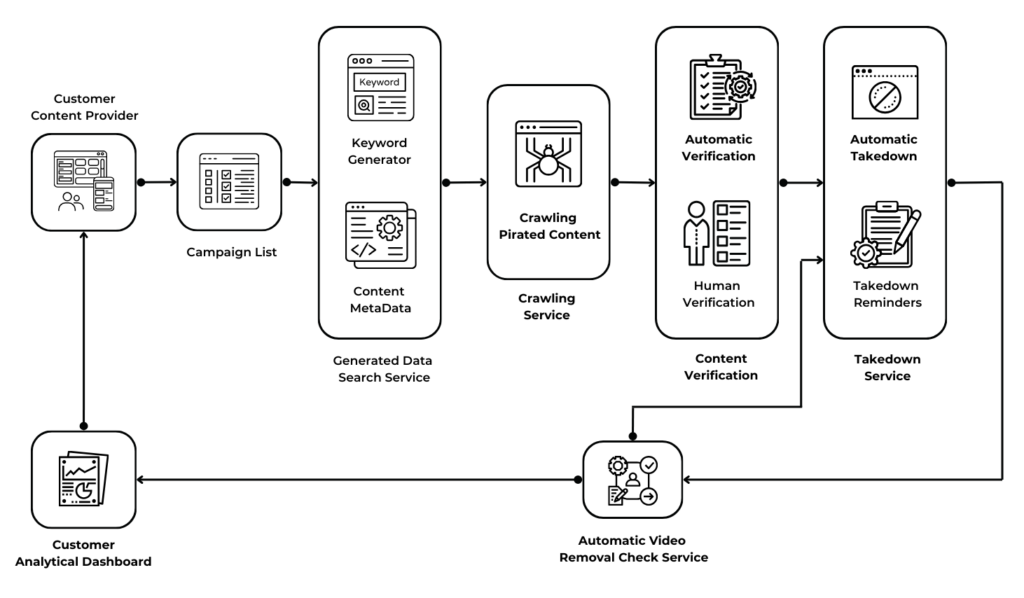
Create Content Monitoring List
The responsibility for providing the assets or content to be monitored or taken down by the system lies with the Customer. they need to provide the necessary materials for the system to be able to search, monitor and takedown
Keyword and Content Metadata Generation
The system will autonomously create the essential keywords and metadata for each content item and seamlessly integrate it into the database, ensuring its accessibility for search functionality.
Searching | Crawling
The system will initiate its search and web crawling activities across the internet, utilizing both keywords and metadata associated with each content to locate sources of videos.
Content Verification
The system will securely store all identified video sources data for subsequent verification, employing a combination of automatic algorithms and human verification techniques to ensure accuracy and reliability.
Collecting Evidences
The system will compile all relevant evidence linked to verified illegal video sources, thereby streamlining the process for issuing takedown notices.
Automated Takedown
The automated takedown system will initiate the process of sending notices to the pertinent Internet Service Providers (ISPs) for each identified content.
Video Removal Detection
The system will automatically conduct verification checks on all video sources, determining their removal status, and then proceed to update this information within the system accordingly.
Takedown Reminders
The system will begin the process of sending reminder notices to the relevant Internet Service Providers (ISPs) for each identified content that remains unremoved after the initial takedown procedure.
Explore Tailored Solutions for Your Business Needs
Explore Tailored Solutions for Your Business Needs
Let's discuss how to safeguard your intellectual property!

